Last week, while conducting an incident response engagement, the iZOOlogic Red Team uncovered one of the most sophisticated OAuth phishing campaigns in our security research experience.
This attack does not steal passwords or bypass MFA. Instead, it tricks users into granting a malicious application complete access to their mailbox through an ingeniously crafted OAuth consent flow.
The Attack Landscape
Initial Discovery
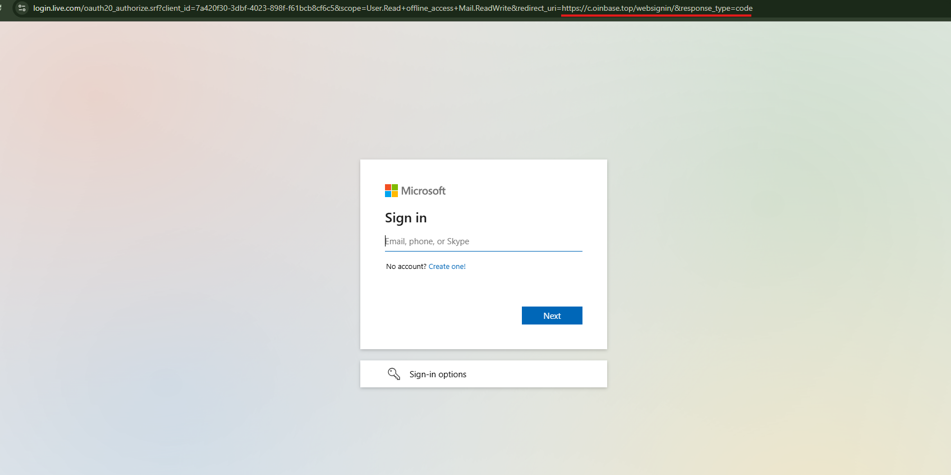
Our investigation began with a suspicious OAuth consent screen reported by a client’s employee. At first glance, it appeared to be a standard Microsoft application request—clean interface, professional design, and all hallmarks of legitimacy. However, our Red Team detected something fundamentally wrong.
Attack Infrastructure
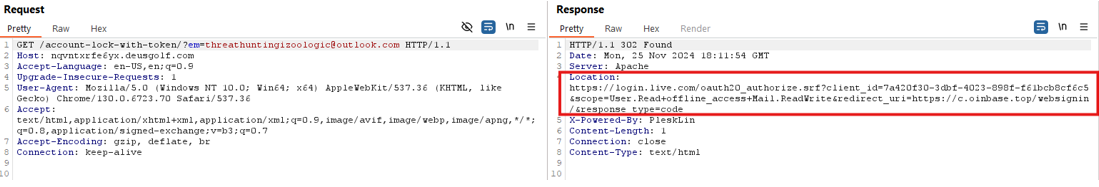
Analyzing the HTTP traffic, we identified the initial redirect chain:
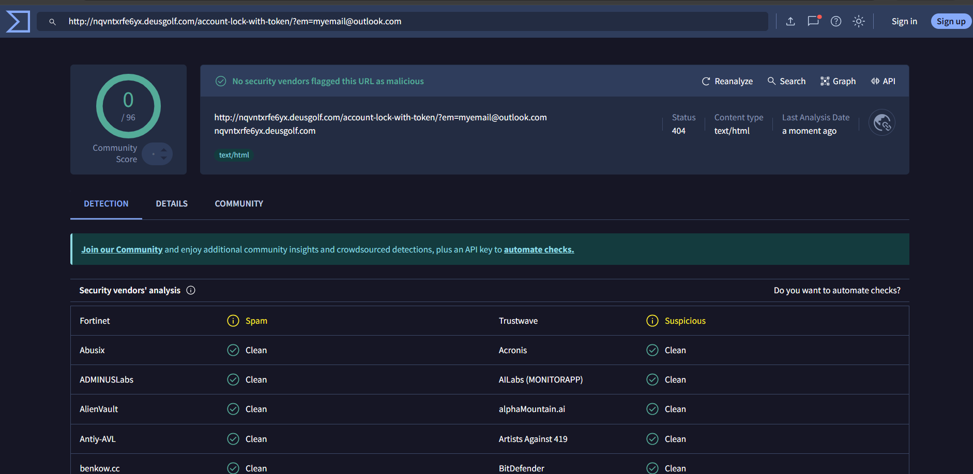
`http://nqvntxrfe6yx[.]deusgolf[.]com/account-lock-with-token/?em=[mail@outlook.com]`
We got zero detections on Virustotal.
(https://www.virustotal.com/gui/url/2f1a5442fab8acc180824c5d22a4be207194eb5d6dbe5452c468415dfc0f4391)
For security professionals, this subdomain immediately raises red flags. It is clearly generated programmatically using Domain Generation Algorithm (DGA) techniques— a classic method used in sophisticated malware campaigns to evade detection.
Attack Flow
The attackers’ methodology is brilliantly simple yet devastatingly effective:
- Send an urgent email about account lockout.
- Drive the victim through a legitimate Microsoft login flow.
- Present a consent screen requesting mailbox permissions.
- Once permissions are granted, achieve persistent mailbox access.
The OAuth Permission Payload
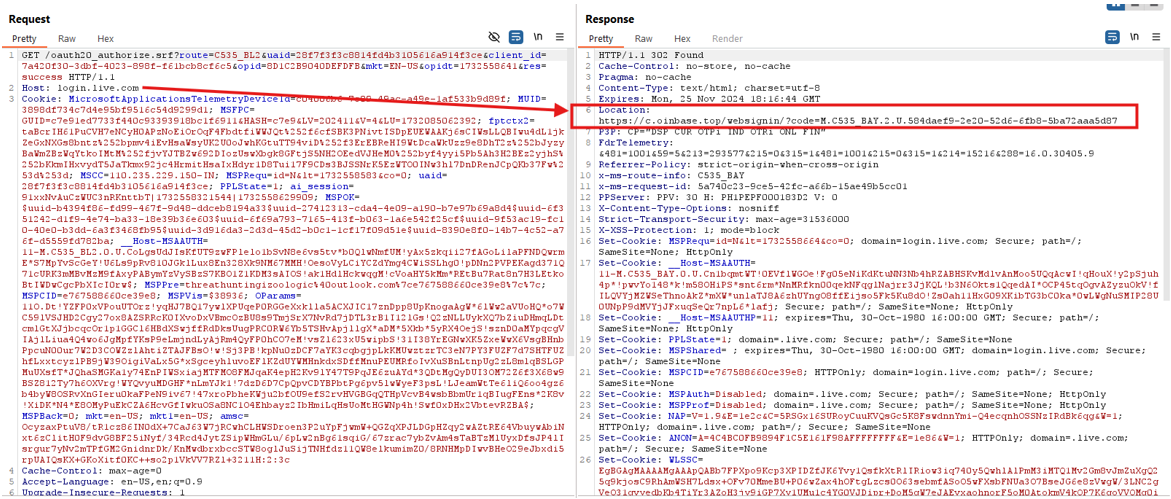
Examining the OAuth permission request revealed the true sophistication:
{
“requested_permissions”: [
“User.Read”,
“offline_access”,
“Mail.ReadWrite”
]
}
The `offline_access` scope is the critical vulnerability. It allows attackers to obtain perpetual refresh tokens, maintaining access even if the victim changes their password.
Infrastructure Analysis
Domain Strategy
The callback domain `c.oinbase.top` demonstrates clever typosquatting. The missing ‘c’ in what should be ‘coinbase’ creates a nearly imperceptible misdirection in the consent screen URL.
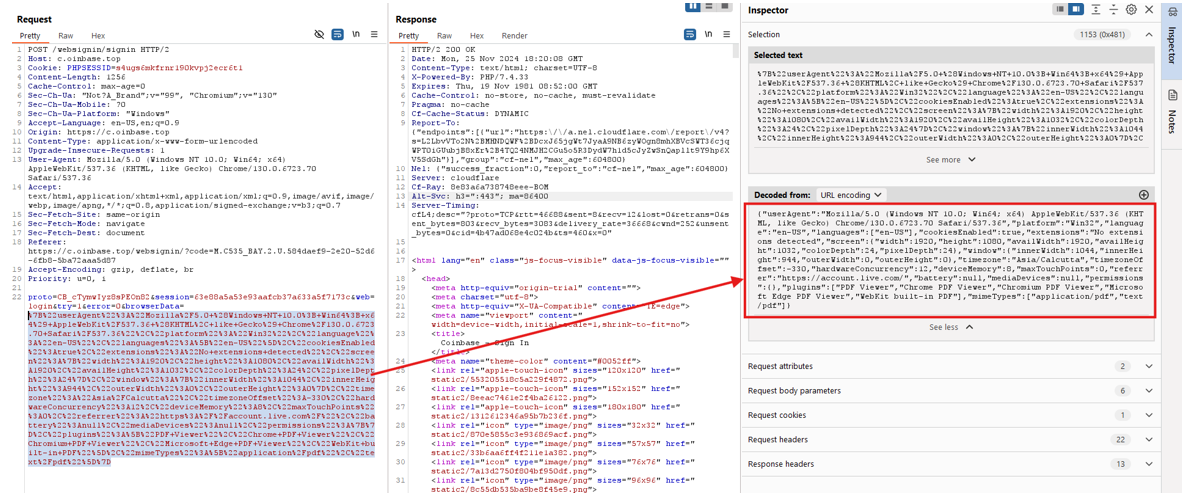
Advanced Browser Fingerprinting
The attackers implemented sophisticated fingerprinting to evade security mechanisms:
{
“deviceMemory”: 8,
“hardwareConcurrency”: 12,
“timezone”: “Asia/Calcutta”,
“userAgent”: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/130.0.6723.70 Safari/537.36”,
“platform”: “Win32”,
“language”: “en-US”,
“languages”: [“en-US”],
“cookiesEnabled”: true,
“extensions”: “No extensions detected”,
“screen”: {
“width”: 1920,
“height”: 1080,
“availWidth”: 1920,
“availHeight”: 1032,
“colorDepth”: 24,
“pixelDepth”: 24
},
“window”: {
“innerWidth”: 1044,
“innerHeight”: 944,
“outerWidth”: 0,
“outerHeight”: 0
},
“timezoneOffset”: -330,
“maxTouchPoints”: 0,
“referrer”: “https://account.live.com/”,
“battery”: null,
“mediaDevices”: null,
“permissions”: {},
“plugins”: [
“PDF Viewer”,
“Chrome PDF Viewer”,
“Chromium PDF Viewer”,
“Microsoft Edge PDF Viewer”,
“WebKit built-in PDF”
],
“mimeTypes”: [
“application/pdf”,
“text/pdf”
]
}
This fingerprinting is not decorative—it’s a strategic tool for detecting and circumventing security sandboxes and automated analysis tools.
Why This Matters to Organisational Security
From iZOOlogic’s perspective, this campaign represents a significant threat evolution:
- Completely bypasses Multi-Factor Authentication.
- Persistence through OAuth token retention.
- Extremely difficult to detect with traditional security tools.
- Exploits gaps in organisational OAuth monitoring.
Defensive Recommendations
OAuth Governance
- Implement strict OAuth permission controls in Microsoft 365.
- Configure application consent restrictions.
- Monitor suspicious OAuth activities:
- Track new application consent grants.
- Watch for unusual redirect URIs.
- Detect multiple consent grants from single applications.
User Training
Educate teams that OAuth permissions are as critical as passwords. Legitimate applications should not request broad mailbox access without clear business justification.
Indicators of Compromise (IOCs)
- Phishing Domain: `nqvntxrfe6yx.deusgolf[.]com`
- OAuth Callback: `c.oinbase[.]top`
Conclusion
This OAuth phishing campaign marks a significant tactical shift in cyber threats. It is sophisticated, effective, and likely to inspire copycat techniques.
The iZOOlogic Red Team will continue monitoring this campaign and update our findings as new intelligence emerges.