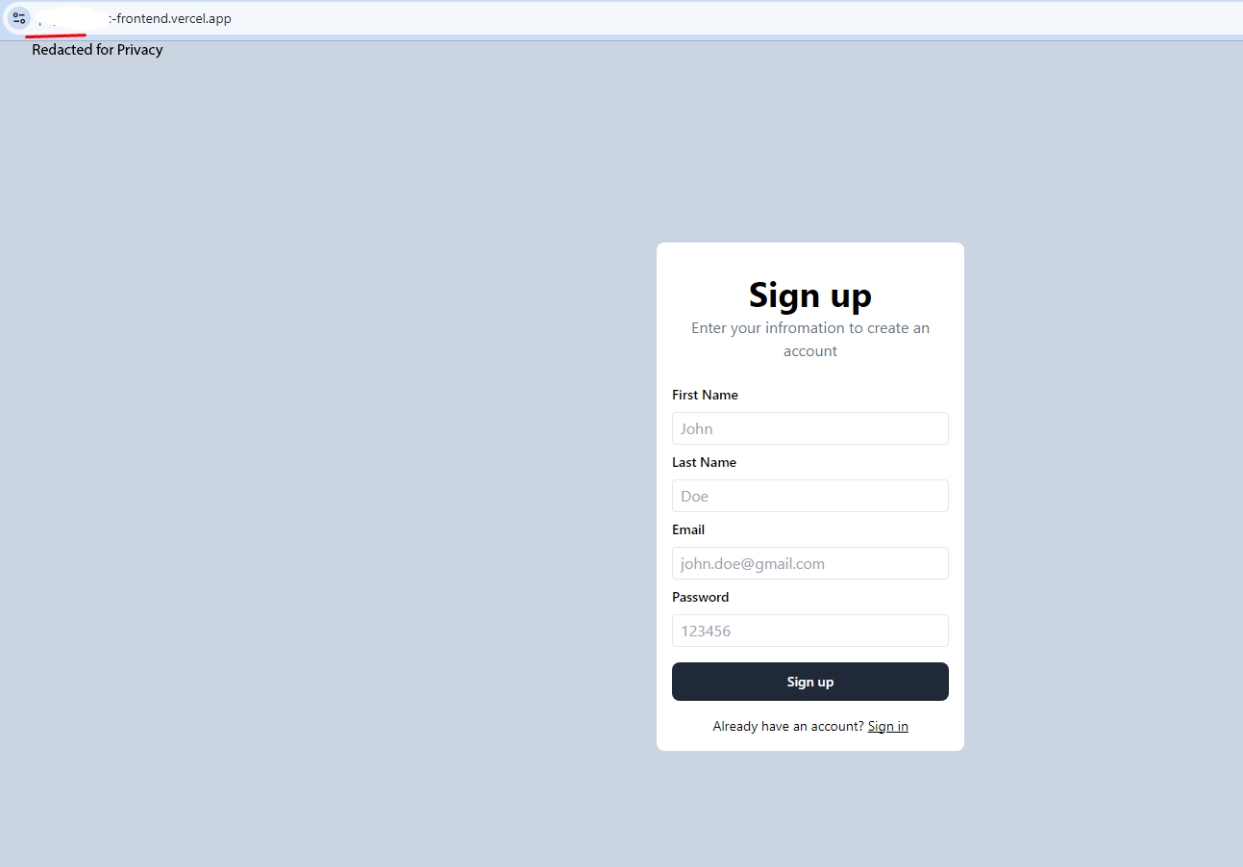
A recent phishing campaign observed by the iZOOlogic SOC Team has been targeting financial institutions in India by abusing the Vercel Platform-as-a-Service (PaaS). The campaign involves malicious actors setting up fraudulent websites that impersonate legitimate financial service providers, aiming to collect sensitive user information such as names, emails, passwords, and even financial details.
Vercel PaaS (Platform-as-a-Service) is a cloud-based platform that allows front-end developers to deploy and manage web applications easily. With support for frameworks like Next.js and React, Vercel offers features such as automatic scaling, a global content delivery network (CDN), and seamless continuous deployment, making it a top choice for creating high-performance websites.
While this specific case involves a financial institution in India, the threat is not limited to this sector. E-commerce, healthcare, and other industries relying on customer trust and sensitive data are equally vulnerable. The misuse of trusted PaaS platforms like Vercel, known for their ease of use and scalability, represents an increasing trend in phishing campaigns, as threat actors take advantage of these platforms’ legitimacy to deceive users at scale.
In this particular attack, the fraudulent website was hosted on the subdomain `<redacted>.basicfrontend.vercel.app`, which mimicked a well-known financial brand. Victims interacting with this site were prompted to enter personal details, which were then transmitted to an unauthorised backend server located at `<redacted>basicbackendone.vercel.app`.
The malicious actors behind this campaign exploited Vercel’s features, such as its free hosting services and global content delivery network (CDN), to easily and cost-effectively reach a large audience. The platform’s SSL certificates, which enable secure HTTPS connections, added another layer of legitimacy to the phishing sites, making them appear more trustworthy to unsuspecting users. The ability to use dynamic subdomains allowed the threat actors to create URLs that closely resembled the legitimate brand, further enhancing the credibility of the attack.
The technical analysis of the phishing site revealed that it collected personal information through standard form inputs, which were then submitted via HTTP POST requests to the malicious backend. The identified indicators of compromise (IOCs) include the domain `<redacted>.basicfrontend.vercel.app` and the API endpoint `<redacted>basicbackendone.vercel.app/api/v1/user/signup`. These details suggest that the phishing site was designed to not only collect user credentials but also enable further fraudulent activities, such as identity theft and financial fraud.
The reach of this campaign goes far beyond individual victims, posing serious risks to businesses, especially in the financial sector. Such attacks can cause considerable reputational damage, as users may mistakenly link the fraudulent site to a legitimate organisation. This erosion of trust can result in long-term repercussions, including the loss of customers and potential regulatory penalties.
Moreover, the financial losses incurred by victims can be substantial, as compromised credentials may allow attackers to conduct unauthorised transactions or commit identity theft. The risks are not confined to the financial sector; other industries with high customer trust, such as healthcare and e-commerce, could also fall victim to similar tactics.
The attackers operating this campaign seem primarily motivated by financial gain, seeking to harvest and profit from user credentials through either direct fraud or by selling the stolen data.
Platform-as-a-Service (PaaS) providers like Vercel appeal to these cybercriminals because of their ease of use, free hosting tiers, and trusted reputation.
With minimal technical expertise required and one-click deployment features, threat actors can rapidly establish phishing sites. The scalability of these platforms also enables them to target a wide range of victims, making PaaS an ideal tool for large-scale phishing operations.
To reduce potential risks, iZOOlogic advises businesses to act fast by immediately requesting the takedown of phishing sites, typically achieving removal within 24 hours. Businesses should also initiate user awareness campaigns to inform and educate their customers about the dangers of engaging with unauthorised websites and how to recognise phishing attempts effectively.
iZOOlogic’s brand monitoring services can help detect similar impersonation attempts in real time, allowing businesses to respond promptly to emerging threats.
For organisations, implementing phishing awareness training is crucial in helping employees and customers recognise phishing sites, particularly those hosted on trusted platforms like Vercel. Encouraging the use of two-factor authentication (2FA) can further protect user accounts, even if credentials are compromised. Security teams should also block the identified IOCs at the network level and harden domain registrations to prevent future misuse of brand names in subdomains.
This phishing campaign highlights the continually evolving strategies employed by cybercriminals and the growing threats faced by businesses across various sectors. iZOOlogic remains vigilant in tracking the progression of this attack and will provide updates as new information becomes available. Effective brand monitoring and swift response efforts are critical to minimising the impact of such phishing campaigns and safeguarding both companies and their customers from potential harm.