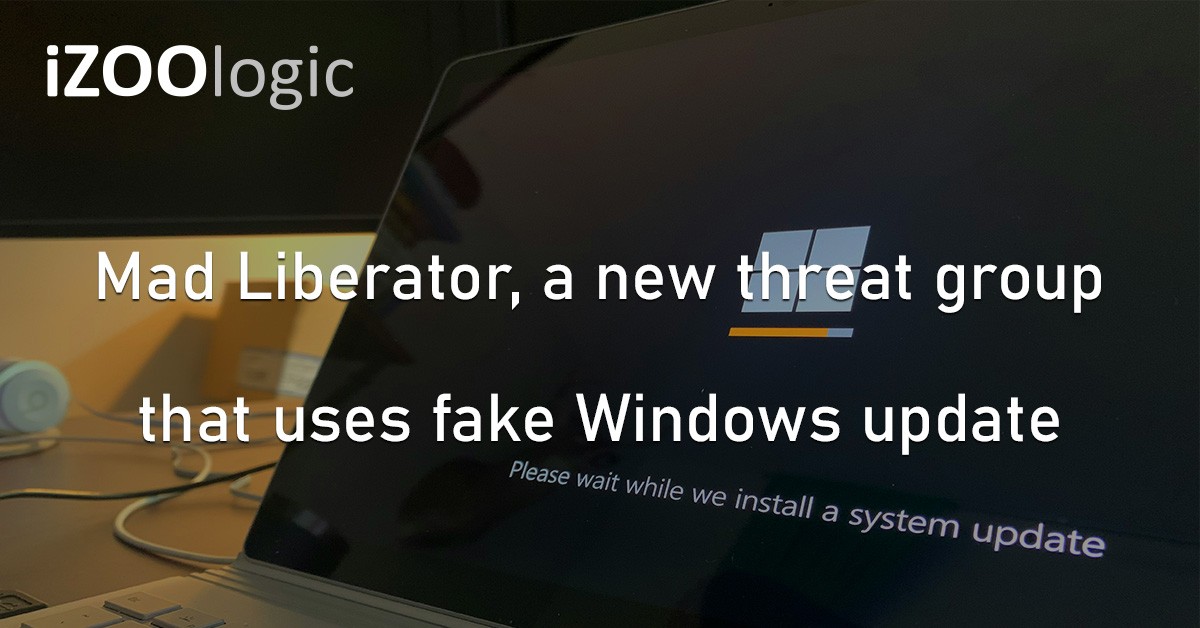
Mad Liberator, a newly discovered malicious entity, targets AnyDesk users using fake MS Windows update pages. Researchers explained that the attackers use this tactic to distract targets while exfiltrating data from the infected device.
Moreover, this operation started in July after the researchers identified one of its activities, encrypting data. The new extortion threat group also revealed on its data leak site that it uses AES/RSA techniques to encrypt information.
Mad Liberator initiates its campaign using AnyDesk.
According to investigations, the Mad Liberator campaign starts with an unauthorised connection to a device through the AnyDesk remote access software.
The initial assessment of the attack states that it could not yet identify how these attackers choose their targets. However, researchers suspect that the Mad Liberator operators try to target several addresses until a user accepts the connection request.
Once a user authorises the connection, the attackers install Microsoft Windows Update malware, which displays a phoney Windows Update splash screen. This technique diverts the user’s attention while the threat actor utilises AnyDesk’s File Transfer tool to steal data from OneDrive accounts, network shares, and local storage. Lastly, the attack disables the victim’s keyboard during the fake update screen to avoid interrupting the exfiltration operation.
In one instance, the researchers noticed that the attackers did not execute data encryption in the post-exfiltration stage. However, it continued distributing ransom notes on shared network directories to ensure maximum visibility in the infected business infrastructure.
Furthermore, Mad Liberator did not communicate with the target before the AnyDesk connection request, and there were no phishing attempts to support the attack.
On the other hand, the group explained on its darknet site that its extortion approach includes communicating with organisations, offering to “help” them fix their security concerns and restore encrypted files if it would provide their monetary demands.
If the victim company does not answer within a day, the threat group will publicise its name on the extortion web and give it a week to contact them. However, the group will publish the stolen files on the Mad Liberator extortion website if the victim does not contact the attackers on days five to seven.
The group has already published nine victims on its extortion site. Therefore, companies should advise their staff to avoid accepting unknown AnyDesk requests to prevent falling victim to this new campaign, Mad Liberator’s primary intrusion tactic.