As cybersecurity experts, we are constantly adapting to the evolving tactics of threat actors. Recently, iZOOlogic encountered a sophisticated phishing campaign targeting a banking institution, which led us to investigate the methods used to inject malicious content into a WordPress environment.
At first glance, what appeared to be a benign site was hiding a cleverly cloaked phishing page that leveraged a vulnerability within the WordPress theme structure to deceive users and evade detection.
Initial Discovery: A Cloaked Phishing Page
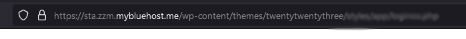
The incident began when a banking client reported suspicious behaviour on a site hosted on Bluehost, using the subdomain sta.zzm.mybluehost.me. The client observed that users visiting the site were sometimes redirected to a phishing page designed to steal login credentials. The URL in question was:
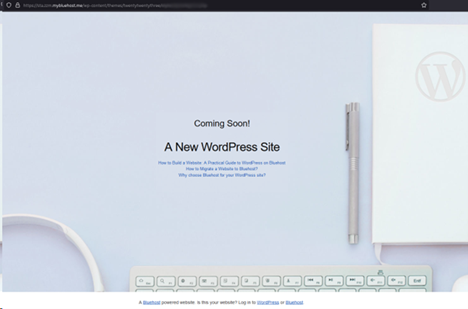
Interestingly, during our initial tests, the page showed only a generic “Coming Soon” WordPress page. However, when the URL was accessed without the “https://” or “http://” protocol, the phishing page was revealed. This was a clear indicator that attackers had employed cloaking techniques to serve different content based on how the site was accessed.
This behaviour suggested a sophisticated evasion tactic aimed at bypassing automated security crawlers, which typically visit URLs using full HTTP/HTTPS protocols. The phishing page was crafted to only appear to users manually typing the URL or accessing it without the protocol, making detection by traditional security measures more difficult.
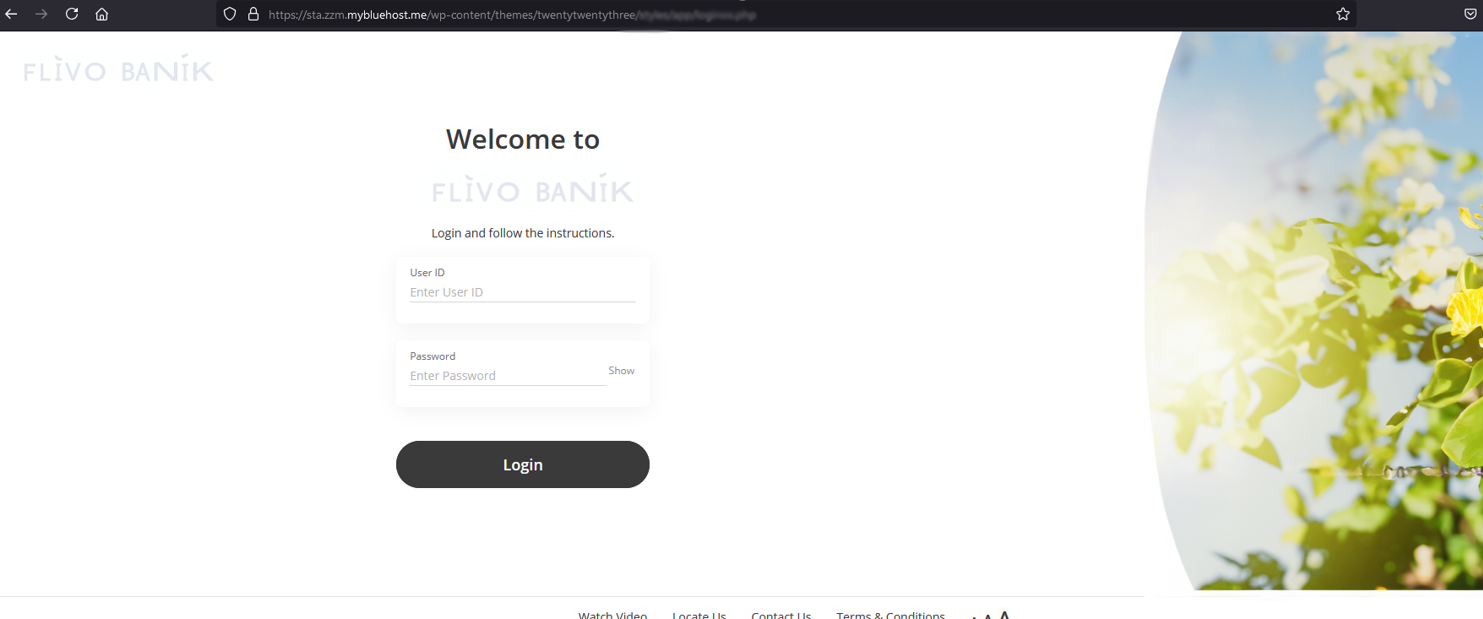
This is how it looked like after unmasking the cloaked content.
Examining the PHP Dynamic Injection Phishing Page
When we got to the phishing page’s source code, we found a PHP script buried in the theme directory (/WP-content/themes/twenty-twentythree). Given that this software was meant to record user inputs in real-time and maybe transmit pilfers of data to a distant server under assault control, its dynamic character was alarming.
Diving deeper into the PHP code helped us realise the following:
- Dynamic content delivery based on user behaviour, possibly determining whether to serve the phishing or benign pages based on specific conditions (e.g., absence of a protocol).
- Cross-domain requests and obfuscated script execution indicated an attempt to manipulate the user’s experience while hiding malicious intent.
- Global execution of scripts, potentially exploiting weaknesses in the WordPress environment or user interactions.
This led us to suspect that the attack was facilitated by an injection of malicious code into the WordPress theme, explicitly targeting vulnerabilities within the site’s configuration or theme files.
Uncovering the WordPress Vulnerability
Our investigation pointed to a common and often overlooked attack vector: WordPress themes and plugins. The phishing page was embedded within the “Twenty Twenty-Three” theme directory, a default WordPress theme. Attackers often exploit outdated or improperly configured themes and plugins to upload malicious files like PHP scripts, which is precisely what happened in this case.
The most likely scenario is that attackers took advantage of one of the following:
- An unpatched vulnerability within the theme or a plugin associated with the site. WordPress themes, especially default or commonly used ones, are frequent targets due to the high volume of sites using them.
- Improper file permissions or unsecured access to the WordPress directory, allowing attackers to upload malicious files or alter existing ones.
- Exploiting outdated versions of WordPress core files, where vulnerabilities in older versions may have allowed attackers to bypass security controls and inject the phishing content.
The Attack Vector: How It Was Done
This phishing attack resulted from an injection of malicious PHP code into the WordPress site, leveraging a theme vulnerability. The attackers likely used one or more of the following methods:
- Exploiting a vulnerable theme: Using the default WordPress theme (“Twenty-Three”) may have made the site susceptible to known vulnerabilities, mainly if updates or patches were not applied in a timely manner.
- Weak file permissions: Improper file permissions could have allowed attackers to directly upload or modify files in the theme directory, creating a backdoor to insert their phishing page.
- Cross-site scripting (XSS) or SQL injection: Attackers could have used XSS or SQL injection to gain unauthorised access to the WordPress admin panel or server, allowing them to modify the theme files and upload malicious content.
- User-agent cloaking: The dynamic PHP script served different content based on how the URL was accessed, specifically targeting users who manually entered the URL without a protocol. This technique allowed the phishing page to evade detection by security scanners and appear legitimate to casual observers.
Mitigating the Threat: A Blue Team Response
As soon as the phishing page was detected, we took immediate action to mitigate the threat:
- Takedown Request: We contacted Bluehost to take down the malicious site and suspend the account hosting the phishing content. Immediate action was required to prevent further credential theft.
- R&D on Advanced Monitoring and Threat Detection: We are currently doing R&D on advanced web traffic monitoring tools to simulate user behaviour from various angles, ensuring that dynamic scripts like the ones used in this attack will be detected in the future.
Key Take Aways
This incident highlights the importance of maintaining a secure WordPress environment, particularly about themes and plugins. WordPress is a powerful and flexible platform, but its popularity makes it a frequent target for attackers.
Key lessons from this experience:
- Keep WordPress, themes, and plugins updated: Vulnerabilities in outdated software are among the most common attack vectors for injecting malicious content.
- Harden file permissions: Ensure that file and directory permissions are configured securely to prevent unauthorised access and modifications.
- Monitor for dynamic content injection: Attackers increasingly use dynamic content delivery mechanisms, like PHP scripts, to serve malicious content only under certain conditions, making traditional detection methods ineffective.
By understanding how attackers exploit WordPress vulnerabilities, the detection and takedowns of such pages could further protect organisations and their customers from similar attacks.